Handling certificate-related issues during offline coding is crucial for Mercedes-Benz diagnostics and repair, and it involves utilizing specialized tools and procedures to ensure secure and accurate vehicle module programming; MERCEDES-DIAGNOSTIC-TOOL.EDU.VN provides the expertise and resources necessary for technicians to navigate these challenges effectively. Properly addressing these issues requires a deep understanding of secure coding practices, diagnostic equipment, and Mercedes-Benz vehicle systems, ensuring that offline coding procedures maintain the highest levels of security and reliability. Contact us via Whatsapp +1 (641) 206-8880 for expert guidance on secure coding and certificate management.
Contents
- 1. What are the Key Considerations for Handling Certificate-Related Issues in Offline Coding?
- 1.1 Understanding Certificate Types
- 1.2 Managing Certificate Validity
- 1.3 Employing Proper Security Protocols
- 1.4 Utilizing Secure Diagnostic Tools
- 2. What Steps Should Be Taken When a Certificate Expires During Offline Coding?
- 2.1 Verifying the Certificate Expiration
- 2.2 Obtaining a Valid Certificate
- 2.3 Updating the Diagnostic Tool
- 2.4 Testing the Certificate
- 2.5 Documentation
- 3. How Can You Troubleshoot “AccountDoesNotExist” Errors During Offline Coding?
- 3.1 Verifying the Let’s Encrypt Setup
- 3.2 Ensuring Correct DNS Settings
- 3.3 Checking the GitLab Configuration
- 3.4 Reviewing Nginx Configuration Files
- 3.5 Checking Let’s Encrypt Account Registration
- 4. What Role Does Nginx Play in Handling SSL Certificates During Offline Coding?
- 4.1 Reverse Proxy Functionality
- 4.2 SSL/TLS Termination
- 4.3 Configuration of SSL Certificates in Nginx
- 4.4 Management of SSL Parameters
- 4.5 Handling Certificate Updates and Renewals
- 5. What Are Common Mistakes to Avoid When Configuring SSL Certificates for Offline Coding?
- 5.1 Using Self-Signed Certificates in Production
- 5.2 Incorrectly Configuring Certificate Paths
- 5.3 Neglecting to Update SSL Parameters
- 5.4 Forgetting to Reload Nginx After Certificate Changes
- 5.5 Not Automating Certificate Renewals
- 5.6 Ignoring Certificate Revocation Lists (CRLs)
- 6. How Do You Implement Certificate Pinning for Enhanced Security During Offline Coding?
- 6.1 Understanding Certificate Pinning
- 6.2 Generating Certificate Hashes
- 6.3 Configuring HTTP Public Key Pinning (HPKP)
- 6.4 Implementing Certificate Pinning in Applications
- 6.5 Testing Certificate Pinning
- 6.6 Managing Certificate Pin Rotations
- 7. How Can You Automate SSL Certificate Management for Offline Coding Environments?
- 7.1 Understanding the Need for Automation
- 7.2 Using Let’s Encrypt and Certbot
- 7.3 Integrating with Configuration Management Tools
- 7.4 Using ACME DNS Challenges
- 7.5 Monitoring Certificate Expiry
- 7.6 Implementing Secure Storage for Certificates
- 8. What Security Best Practices Should Be Followed When Handling Certificates?
- 8.1 Secure Certificate Generation
- 8.2 Secure Certificate Storage
- 8.3 Secure Certificate Usage
1. What are the Key Considerations for Handling Certificate-Related Issues in Offline Coding?
When handling certificate-related issues during offline coding for Mercedes-Benz vehicles, several key considerations ensure secure and successful module programming. These include understanding certificate types, managing certificate validity, and employing proper security protocols.
1.1 Understanding Certificate Types
Different types of certificates are used in Mercedes-Benz vehicle systems, each serving a specific purpose. According to Mercedes-Benz official documentation, understanding these certificates is crucial for ensuring secure communication between the diagnostic tool and the vehicle’s electronic control units (ECUs).
- X.509 Certificates: These are standard digital certificates used for authentication and encryption. They verify the identity of the communicating parties and ensure that data transmitted is secure.
- Code Signing Certificates: These certificates are used to verify the integrity of the software being programmed into the vehicle’s ECUs. They ensure that the software comes from a trusted source and has not been tampered with.
- Root Certificates: These are the top-level certificates in a certificate authority (CA) hierarchy. They are used to verify the authenticity of intermediate and end-entity certificates.
Proper management of these certificate types ensures that only authorized and verified software is used in the vehicle, maintaining its security and functionality.
1.2 Managing Certificate Validity
Certificate validity is a critical aspect of secure offline coding. Certificates have a defined validity period, and using expired certificates can lead to communication failures and security vulnerabilities.
- Regular Updates: Ensure that all certificates used in the offline coding process are up-to-date. According to Mercedes-Benz service bulletins, expired certificates can prevent successful module programming.
- Timestamping: Use timestamping services to ensure that code is considered valid even after the signing certificate has expired. This is particularly important for long-term maintenance and updates.
- Certificate Revocation Lists (CRLs): Regularly check CRLs to ensure that certificates have not been revoked due to compromise or other security issues.
Keeping certificates valid and monitoring their status is essential for preventing disruptions in the offline coding process and maintaining vehicle security.
1.3 Employing Proper Security Protocols
Security protocols are vital for protecting the integrity of the offline coding process. Mercedes-Benz recommends several security measures to prevent unauthorized access and tampering.
- Secure Boot: Implement secure boot processes to ensure that only authorized software is loaded during the vehicle’s startup. This prevents the execution of malicious code.
- Hardware Security Modules (HSMs): Use HSMs to securely store and manage cryptographic keys. HSMs provide a tamper-resistant environment for performing cryptographic operations.
- Access Control: Implement strict access control measures to limit who can perform offline coding and manage certificates. This reduces the risk of insider threats and unauthorized modifications.
By employing these security protocols, technicians can ensure that the offline coding process is secure and that the vehicle’s systems are protected from unauthorized access and tampering.
 Secure Boot Process for Vehicle ECU
Secure Boot Process for Vehicle ECU
1.4 Utilizing Secure Diagnostic Tools
Secure diagnostic tools are essential for handling certificate-related issues in offline coding. These tools are designed to manage certificates securely and ensure that only authorized software is used.
- Mercedes-Benz XENTRY: This is the official diagnostic tool used by Mercedes-Benz. It includes features for managing certificates, performing secure coding, and ensuring that all software updates are authenticated.
- Third-Party Tools: Some third-party tools offer similar capabilities, but it’s crucial to ensure they are authorized and certified by Mercedes-Benz. Using unauthorized tools can compromise vehicle security.
- Regular Updates: Keep diagnostic tools updated to ensure they have the latest security patches and certificate management features.
Using secure and updated diagnostic tools is crucial for maintaining the integrity and security of the offline coding process.
By carefully managing certificate types, validity, and security protocols, and by using secure diagnostic tools, technicians can effectively handle certificate-related issues during offline coding for Mercedes-Benz vehicles. This ensures the security and reliability of the vehicle’s electronic systems. MERCEDES-DIAGNOSTIC-TOOL.EDU.VN offers comprehensive guidance and support for navigating these complex issues, ensuring your Mercedes-Benz vehicle remains secure and performs optimally. Contact us via Whatsapp +1 (641) 206-8880 for expert assistance.
2. What Steps Should Be Taken When a Certificate Expires During Offline Coding?
When a certificate expires during offline coding for Mercedes-Benz vehicles, immediate and precise steps are essential to prevent disruptions and potential security vulnerabilities. Proper handling involves verifying the expiration, obtaining a valid certificate, and updating the diagnostic tool.
2.1 Verifying the Certificate Expiration
The first step is to verify that the certificate has indeed expired. This can be done through the diagnostic tool or by manually checking the certificate details.
- Diagnostic Tool Verification: Mercedes-Benz XENTRY and other authorized diagnostic tools typically provide notifications or error messages indicating certificate expiration.
- Manual Verification: If necessary, the certificate can be manually inspected using standard certificate management tools. The expiration date is clearly indicated in the certificate details.
- Double-Check: Always double-check the date and time settings on the diagnostic tool and the vehicle’s system to ensure they are accurate. Incorrect date/time settings can lead to false expiration alerts.
Verifying the expiration ensures that the appropriate steps are taken based on accurate information, avoiding unnecessary troubleshooting.
2.2 Obtaining a Valid Certificate
Once the expiration is confirmed, the next step is to obtain a valid certificate. This usually involves contacting the certificate authority or the vehicle manufacturer.
- Contacting the Certificate Authority: For standard X.509 certificates, contact the issuing certificate authority to request a renewal or replacement.
- Mercedes-Benz Portal: For vehicle-specific certificates, access the Mercedes-Benz service portal to download the latest valid certificates. According to Mercedes-Benz documentation, this portal is the official source for these certificates.
- Authorized Distributors: Obtain certificates from authorized distributors to ensure their authenticity and validity.
Obtaining a valid certificate from a trusted source is crucial for maintaining the security and integrity of the offline coding process.
2.3 Updating the Diagnostic Tool
After obtaining a valid certificate, the diagnostic tool must be updated with the new certificate. This process varies depending on the tool being used.
- XENTRY Update: In Mercedes-Benz XENTRY, the new certificate can be installed through the certificate management interface. Follow the on-screen instructions to import the certificate.
- Third-Party Tool Update: For third-party tools, consult the tool’s documentation for instructions on how to update certificates. Ensure the tool is compatible with the new certificate format.
- Verification: After updating, verify that the diagnostic tool recognizes the new certificate and that it is marked as valid.
Updating the diagnostic tool ensures that it can properly authenticate and communicate with the vehicle’s ECUs, allowing the offline coding process to proceed smoothly.
 Updating Certificates in Mercedes-Benz XENTRY
Updating Certificates in Mercedes-Benz XENTRY
2.4 Testing the Certificate
Before proceeding with offline coding, it’s important to test the new certificate to ensure it is working correctly.
- Connection Test: Use the diagnostic tool to perform a connection test with the vehicle. This verifies that the tool can establish a secure connection using the new certificate.
- Module Identification: Attempt to identify the vehicle’s modules. Successful identification indicates that the certificate is valid and the tool can communicate with the ECUs.
- Sample Coding: Perform a small, non-critical coding operation to ensure the certificate functions correctly during the coding process.
Testing the certificate helps identify any issues early on, preventing potential problems during critical coding operations.
2.5 Documentation
Finally, document the entire process, including the expiration date of the old certificate, the date the new certificate was obtained, and the steps taken to update the diagnostic tool.
- Record Keeping: Maintain detailed records of all certificate-related activities. This helps with auditing and troubleshooting.
- Compliance: Ensure that the documentation complies with any regulatory or internal requirements for secure coding practices.
- Future Reference: Keep the documentation accessible for future reference. This can be helpful for resolving similar issues in the future.
By following these steps, technicians can effectively handle certificate expirations during offline coding, ensuring the continued security and functionality of Mercedes-Benz vehicles. MERCEDES-DIAGNOSTIC-TOOL.EDU.VN provides comprehensive support and resources to help you manage these critical processes. For personalized assistance, contact us via Whatsapp +1 (641) 206-8880.
3. How Can You Troubleshoot “AccountDoesNotExist” Errors During Offline Coding?
The “AccountDoesNotExist” error during offline coding with tools like GitLab, as seen in the provided context, typically indicates an issue with the Let’s Encrypt configuration. Troubleshooting involves verifying the Let’s Encrypt setup, ensuring correct DNS settings, and checking the GitLab configuration.
3.1 Verifying the Let’s Encrypt Setup
Let’s Encrypt is a certificate authority that provides free SSL/TLS certificates. If your GitLab instance is configured to use Let’s Encrypt, it’s important to ensure that the setup is correct.
- Enable Let’s Encrypt: Ensure that
letsencrypt['enable'] = trueis set in yourgitlab.rbconfiguration file. - Email Configuration: Verify that the
letsencrypt['contact_email']is correctly configured. Let’s Encrypt uses this email to send important notifications about your certificates. - Staging Environment: If you’re using a staging environment, make sure the staging flag is appropriately set.
Ensuring the basic Let’s Encrypt settings are correctly configured is a fundamental step in resolving the “AccountDoesNotExist” error.
3.2 Ensuring Correct DNS Settings
Let’s Encrypt requires that your domain’s DNS settings are correctly configured to point to your server. Incorrect DNS settings can prevent Let’s Encrypt from verifying your domain.
- A Record: Verify that the A record for your domain points to the correct IP address of your server.
- CNAME Record: If you’re using a CNAME record, ensure that it is correctly configured and points to the correct hostname.
- DNS Propagation: After making changes to your DNS settings, allow sufficient time for DNS propagation. This can take up to 48 hours in some cases.
Correct DNS settings are crucial for Let’s Encrypt to validate your domain and issue certificates.
3.3 Checking the GitLab Configuration
GitLab’s configuration must be correctly set up to work with Let’s Encrypt. This includes ensuring that the necessary settings are in place and that GitLab is properly configured to use the certificates.
- External URL: Verify that the
external_urlin yourgitlab.rbfile is correctly set to your domain name (e.g.,https://git.openb.net). - Nginx Configuration: Ensure that the Nginx configuration is properly set up to use the Let’s Encrypt certificates. This typically involves setting the correct paths to the certificate and key files.
- Reconfigure GitLab: After making changes to the
gitlab.rbfile, rungitlab-ctl reconfigureto apply the changes.
A properly configured GitLab instance is essential for seamless integration with Let’s Encrypt.
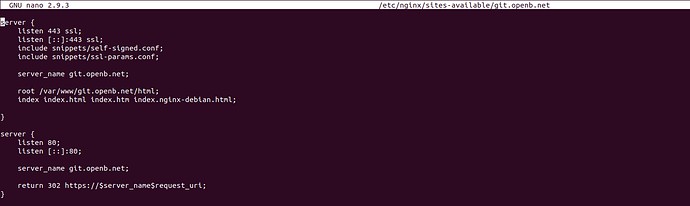
 GitLab Configuration Settings
GitLab Configuration Settings
3.4 Reviewing Nginx Configuration Files
The Nginx configuration files play a critical role in serving your GitLab instance over HTTPS. Reviewing these files can help identify any misconfigurations that might be causing the “AccountDoesNotExist” error.
- ssl-params.conf: Ensure that the
ssl-params.conffile contains the correct SSL settings. This file typically includes settings for SSL protocols, ciphers, and other security parameters. - sites-available/git.openb.net: Verify that the server block in the
sites-available/git.openb.netfile is correctly configured to use the SSL certificates. This includes setting the correct paths to the certificate and key files. - sites-enabled: Ensure that the
git.openb.netfile in thesites-availabledirectory is properly linked to thesites-enableddirectory.
Correct Nginx configuration is vital for serving your GitLab instance securely.
3.5 Checking Let’s Encrypt Account Registration
The “AccountDoesNotExist” error can also occur if the Let’s Encrypt account has not been properly registered. This can happen if the registration process was interrupted or if there was an issue with the Let’s Encrypt service.
- Account Creation: Ensure that the Let’s Encrypt account is created successfully. This typically involves verifying your email address and accepting the Let’s Encrypt terms of service.
- Account Key: Verify that the account key is properly stored and accessible to GitLab. This key is used to authenticate your requests to Let’s Encrypt.
- Re-Registration: If necessary, try re-registering the Let’s Encrypt account. This can help resolve any issues with the initial registration process.
Ensuring that the Let’s Encrypt account is properly registered is crucial for obtaining and renewing certificates.
By systematically verifying the Let’s Encrypt setup, DNS settings, GitLab configuration, Nginx files, and account registration, you can effectively troubleshoot and resolve the “AccountDoesNotExist” error during offline coding with GitLab. MERCEDES-DIAGNOSTIC-TOOL.EDU.VN offers expert guidance on managing such issues, ensuring smooth and secure coding processes. Contact us via Whatsapp +1 (641) 206-8880 for further assistance.
4. What Role Does Nginx Play in Handling SSL Certificates During Offline Coding?
Nginx plays a critical role in handling SSL certificates during offline coding by acting as a reverse proxy and securely serving web content over HTTPS. Its configuration ensures that sensitive data transmitted between the client and server is encrypted and protected.
4.1 Reverse Proxy Functionality
Nginx acts as a reverse proxy, sitting in front of the application server (e.g., GitLab) and handling incoming client requests. This allows Nginx to manage SSL encryption and decryption, offloading this task from the application server.
- Request Handling: Nginx receives incoming HTTPS requests from clients and decrypts the SSL traffic.
- Forwarding Requests: After decryption, Nginx forwards the requests to the application server.
- Response Handling: Nginx receives the responses from the application server and encrypts them using SSL before sending them back to the client.
This reverse proxy setup ensures that the application server only deals with unencrypted traffic, simplifying its configuration and improving performance.
4.2 SSL/TLS Termination
SSL/TLS termination is a key function of Nginx in handling SSL certificates. It involves decrypting incoming SSL traffic and encrypting outgoing traffic.
- Encryption: Nginx uses the SSL certificate and private key to encrypt outgoing traffic, ensuring that it is protected during transmission.
- Decryption: Nginx decrypts incoming SSL traffic, allowing the application server to process the requests.
- Secure Communication: By handling SSL/TLS termination, Nginx ensures that all communication between the client and server is secure.
SSL/TLS termination is essential for protecting sensitive data transmitted over the internet.
4.3 Configuration of SSL Certificates in Nginx
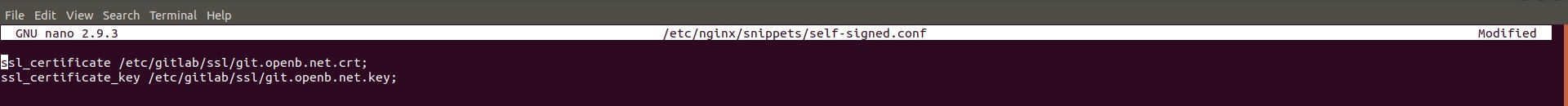
Configuring SSL certificates in Nginx involves specifying the paths to the certificate and key files in the Nginx configuration.
- Certificate Path: The
ssl_certificatedirective specifies the path to the SSL certificate file. - Key Path: The
ssl_certificate_keydirective specifies the path to the SSL private key file. - Example Configuration:
server {
listen 443 ssl;
server_name git.openb.net;
ssl_certificate /etc/gitlab/ssl/git.openb.net.crt;
ssl_certificate_key /etc/gitlab/ssl/git.openb.net.key;
# Other configuration directives
}Correctly configuring these directives ensures that Nginx can properly use the SSL certificate to encrypt and decrypt traffic.
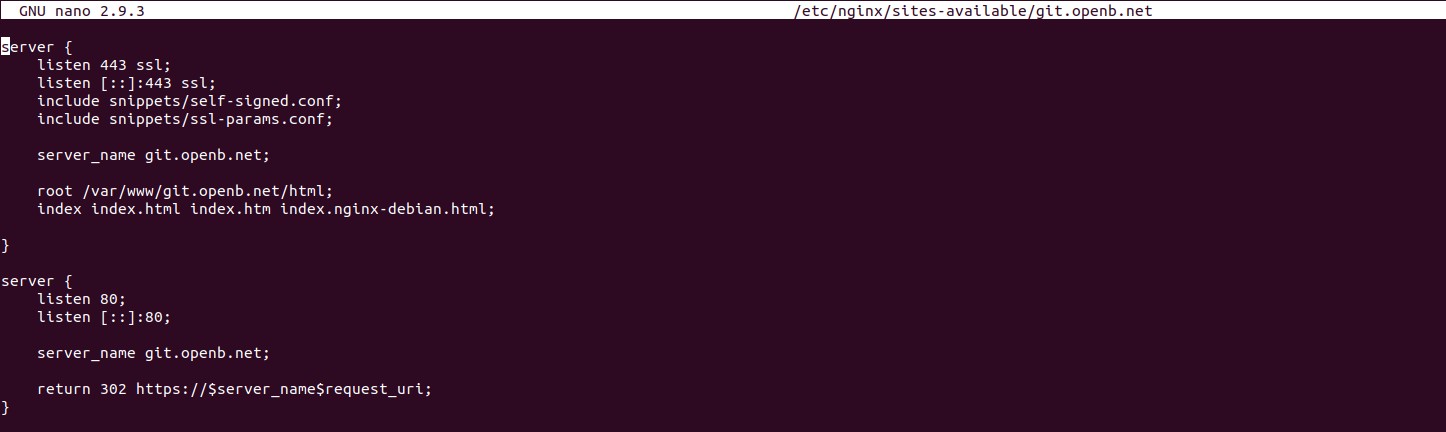 Nginx SSL Configuration
Nginx SSL Configuration
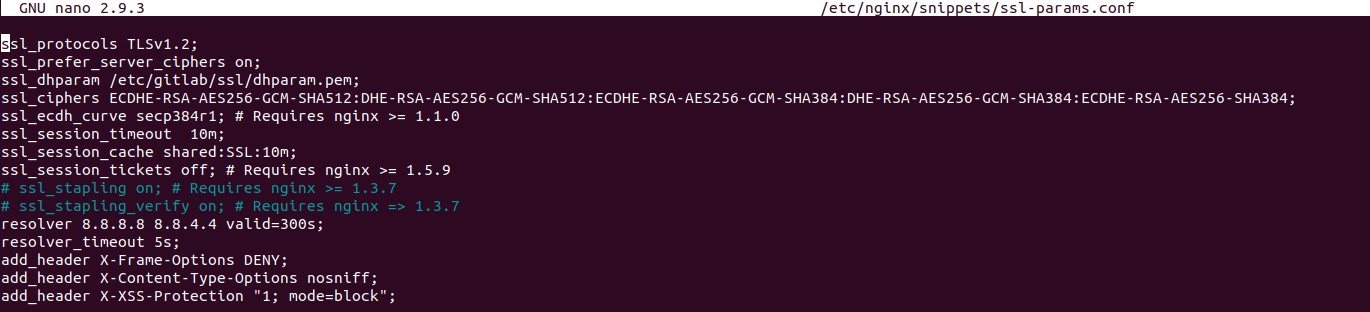
4.4 Management of SSL Parameters
Nginx allows for the management of SSL parameters such as SSL protocols, ciphers, and session settings. These parameters can be configured in the ssl-params.conf file.
- SSL Protocols: The
ssl_protocolsdirective specifies the SSL/TLS protocols that Nginx should use. - SSL Ciphers: The
ssl_ciphersdirective specifies the SSL ciphers that Nginx should use. - SSL Session Settings: Directives such as
ssl_session_cacheandssl_session_timeoutcontrol SSL session caching and timeout settings.
Properly managing these parameters ensures that Nginx uses secure and efficient SSL settings.
4.5 Handling Certificate Updates and Renewals
Nginx must be reconfigured whenever SSL certificates are updated or renewed. This involves updating the paths to the certificate and key files and reloading the Nginx configuration.
- Update Paths: Update the
ssl_certificateandssl_certificate_keydirectives in the Nginx configuration to point to the new certificate and key files. - Reload Configuration: Reload the Nginx configuration using the
nginx -s reloadcommand. This applies the changes without interrupting existing connections. - Automated Renewals: Use tools like Let’s Encrypt’s
certbotto automate the certificate renewal process. These tools can automatically update the Nginx configuration and reload Nginx.
Handling certificate updates and renewals ensures that your Nginx server always uses valid SSL certificates.
By acting as a reverse proxy, handling SSL/TLS termination, configuring SSL certificates, managing SSL parameters, and handling certificate updates, Nginx plays a crucial role in securing offline coding environments. MERCEDES-DIAGNOSTIC-TOOL.EDU.VN provides comprehensive guidance on configuring Nginx for secure coding practices. Contact us via Whatsapp +1 (641) 206-8880 for expert support.
5. What Are Common Mistakes to Avoid When Configuring SSL Certificates for Offline Coding?
Configuring SSL certificates for offline coding can be complex, and several common mistakes can lead to security vulnerabilities and operational issues. Avoiding these mistakes is crucial for maintaining a secure and reliable coding environment.
5.1 Using Self-Signed Certificates in Production
Self-signed certificates are often used for testing and development purposes, but they should never be used in a production environment.
- Lack of Trust: Self-signed certificates are not trusted by web browsers and other clients. This means that users will see warning messages when they access your site.
- Security Risks: Self-signed certificates do not provide the same level of security as certificates issued by a trusted certificate authority.
- Alternatives: Use Let’s Encrypt or purchase a certificate from a trusted certificate authority for production environments.
Using self-signed certificates in production can expose your system to security risks and erode user trust.
5.2 Incorrectly Configuring Certificate Paths
Incorrectly configuring the paths to the certificate and key files in the Nginx configuration is a common mistake.
- File Permissions: Ensure that the Nginx user has read access to the certificate and key files.
- Correct Paths: Double-check that the paths specified in the
ssl_certificateandssl_certificate_keydirectives are correct. - Typos: Watch out for typos in the file paths. Even a small typo can prevent Nginx from loading the certificate.
Incorrectly configured certificate paths can prevent Nginx from using the SSL certificate, leaving your system vulnerable.
5.3 Neglecting to Update SSL Parameters
Failing to update SSL parameters can leave your system vulnerable to outdated SSL protocols and ciphers.
- Outdated Protocols: Ensure that you are using the latest SSL/TLS protocols. Older protocols like SSLv3 and TLS 1.0 have known vulnerabilities.
- Weak Ciphers: Avoid using weak ciphers that are susceptible to attacks.
- Regular Updates: Regularly update your SSL parameters to stay ahead of emerging security threats.
Neglecting to update SSL parameters can expose your system to security vulnerabilities.
 Secure Boot Process for Vehicle ECU
Secure Boot Process for Vehicle ECU
5.4 Forgetting to Reload Nginx After Certificate Changes
Forgetting to reload Nginx after making changes to the SSL configuration is a common mistake.
- Apply Changes: Reloading Nginx applies the changes you have made to the SSL configuration.
- Command: Use the
nginx -s reloadcommand to reload Nginx without interrupting existing connections. - Verification: Verify that the changes have been applied by checking the Nginx error logs.
Forgetting to reload Nginx can prevent your changes from taking effect, leaving your system in an inconsistent state.
5.5 Not Automating Certificate Renewals
Failing to automate certificate renewals can lead to certificate expirations and service disruptions.
- Expiration Dates: Keep track of the expiration dates of your SSL certificates.
- Automation Tools: Use tools like Let’s Encrypt’s
certbotto automate the certificate renewal process. - Renewal Process: Set up a cron job or systemd timer to automatically renew your certificates.
Not automating certificate renewals can lead to unexpected service disruptions and security vulnerabilities.
5.6 Ignoring Certificate Revocation Lists (CRLs)
Ignoring Certificate Revocation Lists (CRLs) can lead to the use of compromised certificates.
- CRLs: CRLs are lists of certificates that have been revoked by the issuing certificate authority.
- Checking CRLs: Regularly check CRLs to ensure that your certificates have not been revoked.
- Automated Checks: Automate the process of checking CRLs to ensure that you are always using valid certificates.
Ignoring CRLs can expose your system to security risks.
By avoiding these common mistakes, you can ensure that your SSL certificates are properly configured and that your offline coding environment is secure and reliable. MERCEDES-DIAGNOSTIC-TOOL.EDU.VN offers expert guidance on avoiding these pitfalls and implementing best practices for SSL certificate management. Contact us via Whatsapp +1 (641) 206-8880 for personalized assistance.
6. How Do You Implement Certificate Pinning for Enhanced Security During Offline Coding?
Implementing certificate pinning enhances security during offline coding by ensuring that the application only trusts specific, pre-approved certificates. This mitigates the risk of man-in-the-middle attacks and unauthorized certificate usage.
6.1 Understanding Certificate Pinning
Certificate pinning is a security technique that involves associating a specific certificate with a domain or application. Instead of trusting any certificate signed by a trusted certificate authority (CA), the application only trusts the pinned certificate.
- Benefits: Certificate pinning provides enhanced security by preventing attackers from using fraudulently obtained certificates to intercept traffic.
- Types of Pinning:
- Public Key Pinning: Pinning the public key of the certificate.
- Certificate Pinning: Pinning the entire certificate.
- Implementation: Certificate pinning can be implemented in various ways, including using HTTP Public Key Pinning (HPKP) or configuring the application to trust only specific certificates.
Understanding the basics of certificate pinning is essential for implementing it effectively.
6.2 Generating Certificate Hashes
The first step in implementing certificate pinning is to generate hashes of the certificates that you want to pin. These hashes will be used to verify the certificates.
- Using OpenSSL: Use OpenSSL to generate the SHA-256 hash of the certificate.
openssl x509 -in certificate.pem -pubkey -noout | openssl pkey -pubin -outform der | openssl dgst -sha256 -binary | openssl enc -base64 - Multiple Certificates: Generate hashes for all certificates in the certificate chain, including the root and intermediate certificates.
- Backup Pins: Generate backup pins in case the primary certificate needs to be replaced.
Generating accurate certificate hashes is crucial for the pinning process.
6.3 Configuring HTTP Public Key Pinning (HPKP)
HTTP Public Key Pinning (HPKP) is a deprecated security feature that allowed web servers to send HTTP headers to instruct clients to pin specific certificates. While HPKP is no longer recommended, understanding it provides context for modern pinning techniques.
- HPKP Header: The
Public-Key-Pinsheader is used to specify the certificate pins.Public-Key-Pins: pin-sha256="base64 hash of certificate"; max-age=expire time; includeSubdomains - Max-Age: The
max-agedirective specifies the amount of time, in seconds, that the client should cache the pins. - IncludeSubdomains: The
includeSubdomainsdirective specifies whether the pins should apply to all subdomains. - Backup Pin: Include a backup pin in case the primary certificate needs to be replaced.
- Deprecation: Note that HPKP is deprecated and should not be used in new deployments. Modern browsers no longer support it due to the risk of denial-of-service attacks if misconfigured.
While HPKP is deprecated, understanding its principles is helpful for implementing modern certificate pinning techniques.
6.4 Implementing Certificate Pinning in Applications
Modern applications implement certificate pinning directly in the application code or configuration. This provides more control and flexibility than HPKP.
-
Code Implementation: Implement certificate pinning in the application code by verifying the certificate hash during the SSL handshake.
-
Configuration Files: Store the certificate hashes in configuration files and load them into the application during startup.
-
Libraries: Use libraries like TrustKit (for iOS and macOS) or similar libraries for other platforms to simplify the implementation of certificate pinning.
-
Example Code:
import ssl import socket def verify_certificate_pin(host, port, pinned_hashes): context = ssl.create_default_context() try: with socket.create_connection((host, port)) as sock: with context.wrap_socket(sock, server_hostname=host) as ssock: cert = ssock.getpeercert(binary_form=True) # Calculate the SHA-256 hash of the certificate import hashlib hash = hashlib.sha256(cert).digest() # Base64 encode the hash import base64 hash_b64 = base64.b64encode(hash).decode('utf-8') if hash_b64 in pinned_hashes: print("Certificate pin verified successfully!") else: raise Exception("Certificate pin verification failed!") except Exception as e: print(f"Error: {e}") # Example usage host = "example.com" port = 443 pinned_hashes = [ "YOUR_CERTIFICATE_HASH_HERE", ] verify_certificate_pin(host, port, pinned_hashes)
Implementing certificate pinning in the application code or configuration provides a more secure and reliable solution than HPKP.
6.5 Testing Certificate Pinning
After implementing certificate pinning, it’s important to test it to ensure that it is working correctly.
- Valid Certificate: Test with a valid, pinned certificate to ensure that the application can establish a connection.
- Invalid Certificate: Test with an invalid or unpinned certificate to ensure that the application rejects the connection.
- Monitoring: Monitor the application logs for certificate pinning failures.
Testing certificate pinning helps identify any issues and ensures that the application is properly secured.
6.6 Managing Certificate Pin Rotations
Certificates expire and need to be rotated periodically. Managing certificate pin rotations is a critical aspect of certificate pinning.
- Backup Pins: Include backup pins in the application configuration to allow for seamless certificate rotations.
- Automated Rotations: Automate the process of rotating certificates and updating the pinned hashes in the application configuration.
- Monitoring: Monitor the application logs for certificate pinning failures during the rotation process.
Properly managing certificate pin rotations ensures that the application remains secure and available.
By understanding certificate pinning, generating certificate hashes, implementing pinning in applications, testing the implementation, and managing certificate rotations, you can effectively enhance security during offline coding. MERCEDES-DIAGNOSTIC-TOOL.EDU.VN offers expert guidance on implementing certificate pinning and other security best practices. Contact us via Whatsapp +1 (641) 206-8880 for personalized assistance.
7. How Can You Automate SSL Certificate Management for Offline Coding Environments?
Automating SSL certificate management for offline coding environments streamlines the process of obtaining, renewing, and deploying SSL certificates, reducing the risk of certificate-related outages and improving security.
7.1 Understanding the Need for Automation
Manual SSL certificate management is time-consuming and error-prone. Automation helps ensure that certificates are always valid and properly configured.
- Reduced Downtime: Automated renewals prevent certificate expirations and service disruptions.
- Improved Security: Automated deployments ensure that the latest security configurations are applied.
- Time Savings: Automation frees up IT staff to focus on other tasks.
Understanding the benefits of automation is the first step in implementing an automated SSL certificate management system.
7.2 Using Let’s Encrypt and Certbot
Let’s Encrypt is a free, automated, and open certificate authority. Certbot is a tool that automates the process of obtaining and renewing Let’s Encrypt certificates.
- Installation: Install Certbot on your server.
sudo apt-get update sudo apt-get install certbot - Obtaining Certificates: Use Certbot to obtain SSL certificates for your domain.
sudo certbot --nginx -d yourdomain.com - Automated Renewals: Certbot can automatically renew certificates using a cron job or systemd timer.
sudo certbot renew --dry-run
Let’s Encrypt and Certbot provide a simple and effective way to automate SSL certificate management.
7.3 Integrating with Configuration Management Tools
Configuration management tools like Ansible, Chef, and Puppet can be used to automate the deployment of SSL certificates and the configuration of web servers.
- Ansible: Use Ansible to automate the process of copying certificates to servers and configuring Nginx or Apache.
- Chef: Use Chef to define the desired state of your SSL configuration and automatically enforce it.
- Puppet: Use Puppet to manage SSL certificates and web server configurations in a declarative manner.
Integrating with configuration management tools provides a scalable and reliable way to automate SSL certificate management.
 Updating Certificates in Mercedes-Benz XENTRY
Updating Certificates in Mercedes-Benz XENTRY
7.4 Using ACME DNS Challenges
ACME DNS challenges allow you to verify domain ownership by adding DNS records. This is useful for automating certificate issuance in environments where HTTP challenges are not possible.
- DNS Provider: Choose a DNS provider that supports ACME DNS challenges.
- Certbot Plugin: Install the Certbot plugin for your DNS provider.
- Configuration: Configure Certbot to use the DNS challenge.
sudo certbot certonly --dns-yourdnsplugin -d yourdomain.com
ACME DNS challenges provide a flexible way to automate certificate issuance in various environments.
7.5 Monitoring Certificate Expiry
Automated monitoring of certificate expiry helps ensure that certificates are renewed before they expire.
- Monitoring Tools: Use monitoring tools like Nagios, Zabbix, or Prometheus to monitor the expiry dates of your SSL certificates.
- Alerting: Configure alerts to notify you when a certificate is approaching its expiry date.
- Automated Renewals: Integrate monitoring with automated renewal processes to ensure that certificates are automatically renewed before they expire.
Monitoring certificate expiry helps prevent certificate-related outages.
7.6 Implementing Secure Storage for Certificates
Securely storing SSL certificates is critical for protecting them from unauthorized access.
- Encryption: Encrypt the SSL certificates using a strong encryption algorithm.
- Access Control: Implement strict access control measures to limit who can access the certificates.
- Hardware Security Modules (HSMs): Use HSMs to securely store and manage cryptographic keys.
Implementing secure storage for certificates helps prevent unauthorized access and tampering.
By using Let’s Encrypt and Certbot, integrating with configuration management tools, using ACME DNS challenges, monitoring certificate expiry, and implementing secure storage, you can effectively automate SSL certificate management for offline coding environments. MERCEDES-DIAGNOSTIC-TOOL.EDU.VN offers expert guidance on implementing these automation techniques. Contact us via Whatsapp +1 (641) 206-8880 for personalized assistance.
8. What Security Best Practices Should Be Followed When Handling Certificates?
Following security best practices when handling certificates is crucial for protecting sensitive data and maintaining the integrity of systems. These practices encompass certificate generation, storage, usage, and monitoring.
8.1 Secure Certificate Generation
Generating certificates securely is the foundation of trust.
- Strong Key Length: Use a strong key length (e.g., 2048 bits or higher for RSA keys, or 256 bits or higher for ECC keys).
- Reputable CA: Obtain certificates from a reputable Certificate Authority (CA).
- Secure Environment: Generate keys in a secure environment, preferably on a dedicated machine or Hardware Security Module (HSM).
- Random Number Generation: Ensure a strong source of randomness during key generation.
Secure certificate generation minimizes the risk of key compromise.
8.2 Secure Certificate Storage
Secure storage is paramount to prevent unauthorized access to private keys.
- Encryption at Rest: Encrypt private keys when stored on disk.
- Access Control: Implement strict access control, limiting access to authorized personnel only.
- HSM: Use Hardware Security Modules (HSMs) for storing and managing private keys.
- Regular Audits: Conduct regular audits to ensure storage security.
Secure certificate storage protects private keys from theft or misuse.
8.3 Secure Certificate Usage
Using certificates securely ensures that they are not misused.
- Principle of Least Privilege: Grant only the necessary privileges to applications and users.
- Short Validity Periods: Use short validity periods for certificates to reduce the window of opportunity for misuse.
- Certificate Pinning: Implement certificate pinning to prevent man-in-the-middle attacks.
- Regular Rotation: Rotate certificates regularly to minimize the impact of potential compromises.
Secure certificate usage prevents unauthorized access and mitigates