A checksum in coding, as explained by MERCEDES-DIAGNOSTIC-TOOL.EDU.VN, is a crucial value used to detect errors in data transmissions by verifying data integrity. This process helps ensure that your Mercedes-Benz diagnostic data remains unaltered, providing accurate results and preventing potential issues. Understanding checksums is vital for anyone involved in coding, automotive diagnostics, or data management.
Contents
- 1. Understanding the Basics of Checksums
- 1.1. What is a Checksum?
- 1.2. How Checksums Work?
- 1.3. The Role of Algorithms in Checksums
- 2. Why Are Checksums Important?
- 2.1. Data Integrity
- 2.2. Error Detection
- 2.3. Preventing Data Corruption
- 3. Checksum Applications and Use Cases
- 3.1. Network Communications
- 3.2. Data Storage
- 3.3. Software Distribution
- 3.4. Automotive Diagnostics
- 3.5. Cybersecurity
- 4. How to Calculate Checksums
- 4.1. Simple Checksum Calculation
- 4.2. Cyclic Redundancy Check (CRC)
- 4.3. MD5 and SHA
- 5. Common Types of Checksum Algorithms
- 5.1. Adler-32
- 5.2. Fletcher Checksum
- 5.3. Cyclic Redundancy Check (CRC)
- 5.4. MD5 (Message Digest Algorithm 5)
- 5.5. SHA (Secure Hash Algorithm)
- 6. How to Verify Checksums
- 6.1. Verifying MD5 Checksums on Windows
- 6.2. Verifying MD5 Checksums on macOS
- 6.3. Verifying SHA Checksums
- 7. What Can Cause an Inconsistent Checksum Number?
- 7.1. Network Interruptions
- 7.2. Storage Issues
- 7.3. Corrupted Files
- 7.4. Third-Party Interference
- 8. Advantages and Disadvantages of Checksums
- 8.1. Advantages of Checksums
- 8.2. Disadvantages of Checksums
- 9. Checksums in Automotive Diagnostics
- 9.1. ECU Programming
- 9.2. Diagnostic Data Transmission
- 9.3. Data Storage
- 10. Best Practices for Using Checksums
- 10.1. Choose the Right Algorithm
- 10.2. Regularly Verify Checksums
- 10.3. Implement Error Correction Mechanisms
- 10.4. Secure Checksum Values
- 10.5. Stay Updated with the Latest Security Practices
- 11. The Future of Checksums
- 11.1. Quantum-Resistant Checksums
- 11.2. AI-Powered Checksums
- 11.3. Blockchain-Based Checksums
- 12. How MERCEDES-DIAGNOSTIC-TOOL.EDU.VN Utilizes Checksums
- 12.1. Ensuring Accurate Diagnostic Data
- 12.2. Preventing Data Corruption
- 12.3. Enhancing Customer Satisfaction
- 13. Frequently Asked Questions (FAQ) About Checksums
- 14. Conclusion: The Essential Role of Checksums
1. Understanding the Basics of Checksums
Checksums play a vital role in ensuring data accuracy and reliability. This is especially important in automotive diagnostics, where precise data is critical for identifying and resolving issues in Mercedes-Benz vehicles.
1.1. What is a Checksum?
A checksum is a small-sized block of data derived from another block of digital data for the purpose of detecting errors that may have been introduced during its transmission or storage. By comparing the checksum of the original data with the checksum of the received data, one can detect alterations.
1.2. How Checksums Work?
Checksums function by generating a unique value from the data before transmission. This value, typically a string of letters and numbers, is calculated using a specific algorithm and appended to the data packet.
Data Packet + Checksum ValueAt the receiving end, the same algorithm is applied to the received data. The newly calculated checksum is then compared to the original checksum. If the two values match, the data is considered intact. If they differ, it indicates that the data has been corrupted or tampered with.
1.3. The Role of Algorithms in Checksums
Checksum algorithms are mathematical functions that produce a checksum value. Various algorithms exist, each with different strengths and weaknesses in detecting errors.
- Simple Checksum: Adds all bytes in a message.
- Cyclic Redundancy Check (CRC): A more sophisticated algorithm that provides better error detection capabilities.
- MD5 and SHA: Cryptographic hash functions used for more secure checksums.
2. Why Are Checksums Important?
Checksums are important for maintaining data integrity in various applications, including network communications, data storage, and software distribution.
2.1. Data Integrity
Data integrity refers to the accuracy and consistency of data. Checksums ensure that the data remains unchanged during transmission or storage.
2.2. Error Detection
Checksums provide a simple yet effective way to detect errors introduced during data transmission or storage. These errors can occur due to various reasons, such as network interruptions, hardware failures, or software bugs.
2.3. Preventing Data Corruption
By detecting errors early, checksums help prevent data corruption. When an error is detected, the system can request a retransmission of the data, ensuring that the received data is accurate.
3. Checksum Applications and Use Cases
Checksums are used in a wide range of applications to ensure data integrity.
3.1. Network Communications
In network communications, checksums are used to verify that data packets are transmitted without errors. Protocols like TCP and UDP use checksums to ensure reliable data transfer. According to a study by the IEEE, TCP, which incorporates checksums, provides a 99.99% reliability rate in data transmission.
3.2. Data Storage
Checksums are used to verify the integrity of data stored on hard drives, SSDs, and other storage devices. This helps prevent data corruption due to hardware failures or other issues.
3.3. Software Distribution
When distributing software, checksums are used to ensure that the downloaded files are complete and have not been tampered with. This is particularly important for security-sensitive applications.
3.4. Automotive Diagnostics
In automotive diagnostics, checksums are used to verify the integrity of diagnostic data transmitted between the vehicle’s electronic control units (ECUs) and diagnostic tools. Accurate data is critical for identifying and resolving issues in the vehicle. At MERCEDES-DIAGNOSTIC-TOOL.EDU.VN, we understand the importance of checksums in maintaining the accuracy of diagnostic data.
3.5. Cybersecurity
Checksums play a crucial role in cybersecurity by ensuring the integrity of files and data. They help detect unauthorized modifications or tampering, which is essential for maintaining the confidentiality, integrity, and availability (CIA triad) of information.
4. How to Calculate Checksums
Calculating checksums involves using specific algorithms to generate a value from the data. The simplest method is to add all the byte values in a message and use the least-significant byte of the sum as the checksum byte. More complex algorithms like CRC, MD5, and SHA provide better error detection capabilities.
4.1. Simple Checksum Calculation
The simplest way to calculate a checksum is to add all the byte values in a message and use the least-significant byte of the sum as the checksum byte. For example, if the message consists of the bytes [72, 101, 108, 108, 111], the sum of these bytes is 582. The least-significant byte of 582 is 6, which would be the checksum value.
4.2. Cyclic Redundancy Check (CRC)
CRC is a more sophisticated algorithm that provides better error detection capabilities. It involves dividing the data by a specific polynomial and using the remainder as the checksum. The CRC algorithm is widely used in network protocols and data storage systems.
4.3. MD5 and SHA
MD5 (Message Digest Algorithm 5) and SHA (Secure Hash Algorithm) are cryptographic hash functions used to generate checksums. These algorithms produce a fixed-size hash value from the data, which can be used to verify the integrity of the data. MD5 produces a 128-bit hash value, while SHA produces hash values of varying lengths, such as 256 bits (SHA-256) or 512 bits (SHA-512).
5. Common Types of Checksum Algorithms
Several algorithms are commonly used to generate checksum values, each with its own strengths and weaknesses.
5.1. Adler-32
Adler-32 is a checksum algorithm developed by Mark Adler. It is similar to a Fletcher checksum but is faster and provides better error detection capabilities.
5.2. Fletcher Checksum
The Fletcher checksum is a checksum algorithm developed by John Fletcher. It is relatively simple to implement and provides decent error detection capabilities.
5.3. Cyclic Redundancy Check (CRC)
CRC is a widely used checksum algorithm that provides excellent error detection capabilities. It is commonly used in network protocols, data storage systems, and other applications where data integrity is critical.
5.4. MD5 (Message Digest Algorithm 5)
MD5 is a cryptographic hash function that produces a 128-bit hash value. It is commonly used to verify the integrity of files and data. However, MD5 has been found to be vulnerable to collision attacks, so it is not recommended for security-sensitive applications.
5.5. SHA (Secure Hash Algorithm)
SHA is a family of cryptographic hash functions that includes SHA-1, SHA-256, SHA-512, and others. These algorithms produce hash values of varying lengths and provide strong collision resistance. SHA algorithms are widely used in security-sensitive applications, such as digital signatures and password storage.
6. How to Verify Checksums
Verifying checksums involves calculating the checksum of the received data and comparing it to the original checksum. If the two values match, the data is considered intact. If they differ, it indicates that the data has been corrupted or tampered with.
6.1. Verifying MD5 Checksums on Windows
To verify the MD5 hash of a file on Windows, you can use the certutil command in the command prompt.
- Open the command prompt by typing
cmdin the search box and pressing Enter. - Navigate to the folder containing the file by typing
cdfollowed by the path to the folder. - Type
certutil -hashfile <filename> MD5and press Enter. Replace<filename>with the name of the file. - The MD5 hash of the file will be displayed. Compare this value with the expected value to verify the integrity of the file.
6.2. Verifying MD5 Checksums on macOS
To verify the MD5 hash of a file on macOS, you can use the md5 command in the Terminal.
- Open the Terminal.
- Navigate to the folder containing the file by typing
cdfollowed by the path to the folder. - Type
md5 <filename>and press Enter. Replace<filename>with the name of the file. - The MD5 hash of the file will be displayed. Compare this value with the expected value to verify the integrity of the file.
6.3. Verifying SHA Checksums
Verifying SHA checksums is similar to verifying MD5 checksums. You can use the certutil command on Windows or the shasum command on macOS to calculate and verify SHA hash values.
7. What Can Cause an Inconsistent Checksum Number?
Several factors can cause checksum values to be inconsistent, indicating that the data has been corrupted or tampered with.
7.1. Network Interruptions
Interruptions in the network connection during data transmission can cause data packets to be lost or corrupted, resulting in an inconsistent checksum.
7.2. Storage Issues
Problems with the hard drive or other storage devices can cause data corruption, leading to inconsistent checksum values.
7.3. Corrupted Files
Files can become corrupted due to various reasons, such as software bugs, hardware failures, or viruses. Corrupted files will have inconsistent checksum values.
7.4. Third-Party Interference
Malicious third parties can interfere with data transmission or storage, tampering with the data and causing inconsistent checksum values.
8. Advantages and Disadvantages of Checksums
Checksums offer several advantages and disadvantages in terms of data integrity and security.
8.1. Advantages of Checksums
- Simple and Efficient: Checksums are relatively simple to calculate and verify, making them an efficient way to detect errors.
- Early Warning: Checksums provide an early warning of data corruption, allowing users to take corrective action before data loss occurs.
- Data Integrity Verification: Checksums ensure that data remains unchanged during transmission or storage, maintaining data integrity.
8.2. Disadvantages of Checksums
- Limited Error Detection: Checksums may not detect all types of errors, such as byte rearrangements or missing bytes.
- Vulnerable to Manipulation: Checksum values can be manipulated or forged by malicious parties, making them inadequate for ensuring data integrity in security-sensitive applications.
- No Error Correction: Checksums can only detect errors but do not provide a mechanism to fix them.
- Overhead: Checksum calculations add complexity and overhead to the data transfer process.
9. Checksums in Automotive Diagnostics
In automotive diagnostics, checksums are used to ensure the integrity of diagnostic data transmitted between the vehicle’s ECUs and diagnostic tools. Accurate data is critical for identifying and resolving issues in the vehicle.
9.1. ECU Programming
When programming or updating the software in an ECU, checksums are used to verify that the new software is transmitted without errors. This ensures that the ECU functions correctly after the update.
9.2. Diagnostic Data Transmission
During diagnostic data transmission, checksums are used to verify that the data packets are transmitted without errors. This ensures that the diagnostic tool receives accurate information about the vehicle’s systems.
9.3. Data Storage
Checksums are used to verify the integrity of diagnostic data stored in the vehicle’s memory or in diagnostic databases. This ensures that the data remains accurate and reliable over time.
10. Best Practices for Using Checksums
To ensure the effectiveness of checksums, it is important to follow best practices for their implementation and use.
10.1. Choose the Right Algorithm
Select the appropriate checksum algorithm based on the application’s requirements. For applications requiring high error detection capabilities, use CRC or SHA algorithms. For security-sensitive applications, use SHA algorithms.
10.2. Regularly Verify Checksums
Regularly verify checksums to detect data corruption early. This is particularly important for data stored over long periods or transmitted over unreliable networks.
10.3. Implement Error Correction Mechanisms
In addition to checksums, implement error correction mechanisms to fix errors when they are detected. This can involve retransmitting data or using more sophisticated error correction codes.
10.4. Secure Checksum Values
Protect checksum values from manipulation by malicious parties. This can involve using cryptographic hash functions and storing checksum values securely.
10.5. Stay Updated with the Latest Security Practices
Keep up-to-date with the latest security practices and checksum algorithms to ensure that your data remains protected from emerging threats.
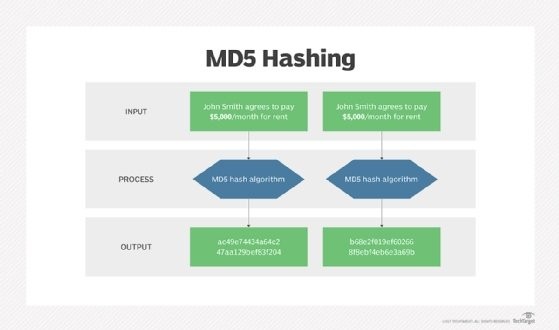 Diagram illustrating the steps in MD5 Hashing, input, process, output
Diagram illustrating the steps in MD5 Hashing, input, process, output
11. The Future of Checksums
As technology evolves, checksums will continue to play a critical role in ensuring data integrity. New checksum algorithms and techniques are being developed to address emerging threats and improve error detection capabilities.
11.1. Quantum-Resistant Checksums
With the development of quantum computers, existing cryptographic hash functions may become vulnerable to attacks. Researchers are working on developing quantum-resistant checksum algorithms that can withstand attacks from quantum computers.
11.2. AI-Powered Checksums
Artificial intelligence (AI) and machine learning (ML) can be used to improve checksum algorithms and error detection capabilities. AI-powered checksums can analyze data patterns and detect subtle errors that traditional checksums may miss.
11.3. Blockchain-Based Checksums
Blockchain technology can be used to create decentralized and tamper-proof checksum systems. By storing checksum values on a blockchain, it becomes virtually impossible for malicious parties to manipulate or forge them.
12. How MERCEDES-DIAGNOSTIC-TOOL.EDU.VN Utilizes Checksums
At MERCEDES-DIAGNOSTIC-TOOL.EDU.VN, we prioritize data accuracy and reliability in all our diagnostic services. We utilize checksums to ensure that the diagnostic data transmitted between the vehicle’s ECUs and our diagnostic tools remains unaltered and accurate.
12.1. Ensuring Accurate Diagnostic Data
By verifying the checksum of diagnostic data, we ensure that the information we receive is accurate and reliable. This allows us to make informed decisions about the vehicle’s condition and provide effective solutions.
12.2. Preventing Data Corruption
Checksums help us prevent data corruption during diagnostic data transmission. If an error is detected, we request a retransmission of the data, ensuring that we receive accurate information.
12.3. Enhancing Customer Satisfaction
By ensuring the accuracy and reliability of our diagnostic services, we enhance customer satisfaction. Our customers can trust that the information we provide is accurate and that we are committed to providing the best possible service.
13. Frequently Asked Questions (FAQ) About Checksums
13.1. What is the purpose of a checksum?
A checksum is used to detect errors in data transmission or storage by verifying data integrity.
13.2. How do checksums work?
Checksums work by generating a unique value from the data before transmission and comparing it to the value calculated from the received data.
13.3. What are common types of checksum algorithms?
Common types of checksum algorithms include Adler-32, Fletcher checksum, CRC, MD5, and SHA.
13.4. How can I verify checksums on Windows?
You can verify checksums on Windows using the certutil command in the command prompt.
13.5. How can I verify checksums on macOS?
You can verify checksums on macOS using the md5 or shasum command in the Terminal.
13.6. What can cause an inconsistent checksum number?
Inconsistent checksum numbers can be caused by network interruptions, storage issues, corrupted files, or third-party interference.
13.7. What are the advantages of using checksums?
Advantages of using checksums include simplicity, efficiency, early warning of data corruption, and data integrity verification.
13.8. What are the disadvantages of using checksums?
Disadvantages of using checksums include limited error detection, vulnerability to manipulation, no error correction, and overhead.
13.9. How are checksums used in automotive diagnostics?
Checksums are used in automotive diagnostics to ensure the integrity of diagnostic data transmitted between the vehicle’s ECUs and diagnostic tools.
13.10. What are some best practices for using checksums?
Best practices for using checksums include choosing the right algorithm, regularly verifying checksums, implementing error correction mechanisms, and securing checksum values.
14. Conclusion: The Essential Role of Checksums
Checksums are an essential tool for ensuring data integrity and preventing data corruption in a wide range of applications. By understanding how checksums work and following best practices for their implementation, you can protect your data and ensure its accuracy and reliability.
At MERCEDES-DIAGNOSTIC-TOOL.EDU.VN, we are committed to providing accurate and reliable diagnostic services for Mercedes-Benz vehicles. We utilize checksums to ensure that the diagnostic data we receive is accurate and that our customers can trust the information we provide.
Ensure the integrity of your Mercedes-Benz diagnostic data with MERCEDES-DIAGNOSTIC-TOOL.EDU.VN. Contact us today for expert diagnostics and reliable solutions.
For further assistance with your Mercedes-Benz diagnostics and to ensure the accuracy of your data, reach out to us. Visit our website at MERCEDES-DIAGNOSTIC-TOOL.EDU.VN, contact us via WhatsApp at +1 (641) 206-8880, or visit our location at 789 Oak Avenue, Miami, FL 33101, United States. Let MERCEDES-DIAGNOSTIC-TOOL.EDU.VN help you maintain the peak performance and reliability of your Mercedes-Benz.