Cybersecurity in modern vehicle diagnostics is paramount, protecting sensitive vehicle data and preventing unauthorized access that could compromise safety systems; MERCEDES-DIAGNOSTIC-TOOL.EDU.VN offers expert insights and tools to navigate this complex landscape. By understanding cybersecurity’s vital role, you can ensure the safety, security, and longevity of your Mercedes-Benz. Explore vehicle network protection, data encryption, and secure access to diagnostic ports.
Contents
- 1. Understanding the Growing Cybersecurity Threat to Vehicles
- 1.1 What Makes Modern Vehicles Vulnerable to Cyberattacks?
- 1.2 How Can These Vulnerabilities Be Exploited?
- 1.3 What are the Potential Consequences of a Vehicle Cyberattack?
- 2. The Role of Cybersecurity in Vehicle Diagnostics
- 2.1 How Does Cybersecurity Protect Diagnostic Processes?
- 2.2 What Security Measures Are Incorporated into Diagnostic Tools?
- 2.3 How Does Cybersecurity Prevent Unauthorized Access During Diagnostics?
- 3. Key Cybersecurity Practices for Vehicle Diagnostics
- 3.1 What is Domain Separation and Why is It Important?
- 3.2 How Can Secure Communication Be Ensured During Diagnostics?
- 3.3 What is the Role of Continuous Monitoring in Cybersecurity?
- 3.4 How Does MERCEDES-DIAGNOSTIC-TOOL.EDU.VN Assist in Implementing These Practices?
- 4. Technologies Used to Mitigate Vehicle Cybersecurity Vulnerabilities
- 4.1 What is Message Encryption and How Does It Work?
- 4.2 How Do Intrusion Detection Systems Protect Vehicles?
- 4.3 Why Are Secure Over-the-Air (OTA) Updates Important?
- 4.4 How Does MERCEDES-DIAGNOSTIC-TOOL.EDU.VN Support the Use of These Technologies?
- 5. Addressing the Challenges of Vehicle Cybersecurity
- 5.1 What Are the Key Challenges in Vehicle Cybersecurity?
- 5.2 How Can These Challenges Be Addressed?
- 5.3 What Industry-Led Efforts Are Underway to Improve Vehicle Cybersecurity?
- 5.4 How Does MERCEDES-DIAGNOSTIC-TOOL.EDU.VN Contribute to Overcoming These Challenges?
- 6. The Role of Regulatory Bodies in Vehicle Cybersecurity
- 6.1 What Actions Has NHTSA Taken to Address Vehicle Cybersecurity?
- 6.2 What Future Actions Are Planned by Regulatory Bodies?
- 6.3 How Does MERCEDES-DIAGNOSTIC-TOOL.EDU.VN Stay Informed About Regulatory Changes?
- 7. Best Practices for Maintaining Vehicle Cybersecurity
- 7.1 Why Are Regular Software Updates Important?
- 7.2 How Can Secure Diagnostic Practices Be Implemented?
- 7.3 What Should Vehicle Owners Know About Cybersecurity?
- 7.4 How Does MERCEDES-DIAGNOSTIC-TOOL.EDU.VN Educate Vehicle Owners?
- 8. The Future of Cybersecurity in Vehicle Diagnostics
- 8.1 What Trends Are Shaping the Future of Vehicle Cybersecurity?
- 8.2 How Will These Trends Impact Vehicle Diagnostics?
- 8.3 How is MERCEDES-DIAGNOSTIC-TOOL.EDU.VN Preparing for the Future?
- 9. Case Studies of Vehicle Cyberattacks
- 9.1 What Are Some Notable Examples of Vehicle Cyberattacks?
- 9.2 What Lessons Can Be Learned from These Attacks?
- 9.3 How Can MERCEDES-DIAGNOSTIC-TOOL.EDU.VN Help Prevent Similar Attacks?
- 10. FAQs About Cybersecurity in Vehicle Diagnostics
- 10.1 What is the Biggest Cybersecurity Threat to My Mercedes-Benz?
- 10.2 How Can I Tell if My Vehicle Has Been Hacked?
- 10.3 What Should I Do if I Suspect My Vehicle Has Been Hacked?
- 10.4 Are Older Vehicles Less Vulnerable to Cyberattacks?
- 10.5 How Often Should I Update My Vehicle’s Software?
- 10.6 Can a Diagnostic Tool Introduce a Virus into My Vehicle?
- 10.7 What is the Role of the OBD Port in Vehicle Cybersecurity?
- 10.8 How Does Encryption Protect My Vehicle’s Data?
- 10.9 What is Multi-Factor Authentication and Why is It Important?
- 10.10 Where Can I Find More Information About Vehicle Cybersecurity?
1. Understanding the Growing Cybersecurity Threat to Vehicles
Modern vehicles are increasingly connected, relying on extensive software and network communication to manage various functions. This connectivity, while enhancing convenience and performance, also exposes vehicles to potential cyber threats. As the Government Accountability Office (GAO) points out, multiple interfaces, including wireless connections and the on-board diagnostics (OBD) port, can be exploited by malicious actors.
The increasing sophistication of these systems makes them attractive targets, necessitating robust cybersecurity measures to protect against unauthorized access and manipulation. This is especially critical for safety-critical systems such as braking, steering, and engine control, where a compromise could lead to severe consequences.
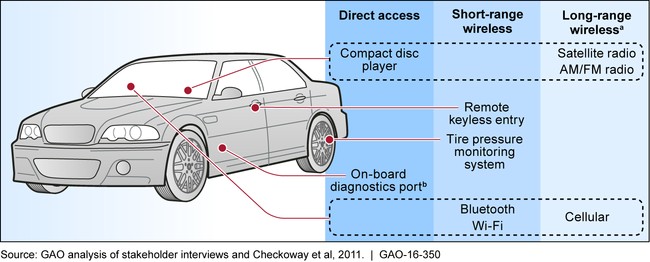 Key Vehicle Interfaces That Could Be Exploited in a Vehicle Cyberattack
Key Vehicle Interfaces That Could Be Exploited in a Vehicle Cyberattack
1.1 What Makes Modern Vehicles Vulnerable to Cyberattacks?
Modern vehicles are vulnerable due to several factors:
- Increased Connectivity: Vehicles now feature multiple wireless interfaces such as Bluetooth, cellular, and Wi-Fi, providing numerous entry points for attackers.
- Complex Software: The sheer volume of software code in modern vehicles increases the likelihood of vulnerabilities.
- On-Board Diagnostics (OBD) Port: The OBD port, while essential for diagnostics and emissions testing, offers direct access to critical vehicle systems.
1.2 How Can These Vulnerabilities Be Exploited?
Exploitation can occur through:
- Direct Physical Access: Attackers can gain access via the OBD port.
- Short-Range Wireless Channels: Bluetooth vulnerabilities can be exploited to access in-vehicle networks.
- Long-Range Wireless Channels: Cellular connections can be compromised to remotely control vehicle functions from anywhere in the world.
1.3 What are the Potential Consequences of a Vehicle Cyberattack?
The consequences can be severe, including:
- Compromised Safety Systems: Manipulation of braking, steering, or engine control could lead to accidents.
- Data Theft: Personal and vehicle data can be stolen, leading to privacy breaches.
- Vehicle Immobilization: Attackers can remotely disable a vehicle, causing inconvenience and potential danger.
2. The Role of Cybersecurity in Vehicle Diagnostics
Cybersecurity plays a critical role in vehicle diagnostics by ensuring the integrity and confidentiality of diagnostic data, as well as preventing unauthorized access to vehicle systems during the diagnostic process. Modern diagnostic tools and procedures must incorporate robust security measures to safeguard against potential cyber threats.
2.1 How Does Cybersecurity Protect Diagnostic Processes?
Cybersecurity measures protect diagnostic processes by:
- Securing Communication Channels: Encrypting data transmitted between the diagnostic tool and the vehicle.
- Authenticating Users: Verifying the identity of users accessing diagnostic functions.
- Monitoring Access: Tracking and logging access to diagnostic systems to detect unauthorized activity.
- Protecting Diagnostic Tools: Ensuring that diagnostic tools themselves are secure and free from malware.
2.2 What Security Measures Are Incorporated into Diagnostic Tools?
Modern diagnostic tools incorporate several security measures:
- Data Encryption: Protecting data during transmission and storage.
- User Authentication: Requiring secure login credentials and multi-factor authentication.
- Role-Based Access Control: Limiting access to diagnostic functions based on user roles and permissions.
- Secure Boot: Ensuring that the diagnostic tool’s software has not been tampered with.
- Regular Updates: Keeping the diagnostic tool’s software up-to-date with the latest security patches.
2.3 How Does Cybersecurity Prevent Unauthorized Access During Diagnostics?
Unauthorized access is prevented through:
- Secure Diagnostic Ports: Implementing security protocols for accessing the OBD port.
- Wireless Intrusion Detection: Monitoring wireless communication for suspicious activity.
- Access Logging: Recording all diagnostic sessions to track user activity and identify potential breaches.
- Remote Access Controls: Restricting remote diagnostic access to authorized personnel only.
3. Key Cybersecurity Practices for Vehicle Diagnostics
Implementing key cybersecurity practices is essential for protecting vehicle diagnostic processes from cyber threats. These practices include domain separation, secure communication, and continuous monitoring.
3.1 What is Domain Separation and Why is It Important?
Domain separation involves isolating safety-critical systems from non-safety-critical systems within a vehicle’s network. This separation limits the potential impact of a cyberattack, preventing it from spreading from one domain to another.
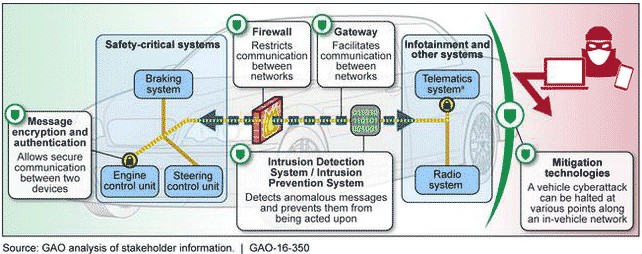 Example of a Vehicle's Cybersecurity-Mitigation Technologies Shown along an In-Vehicle Network
Example of a Vehicle's Cybersecurity-Mitigation Technologies Shown along an In-Vehicle Network
3.2 How Can Secure Communication Be Ensured During Diagnostics?
Secure communication can be ensured through:
- Encryption: Using strong encryption algorithms to protect data transmitted between diagnostic tools and the vehicle.
- Authentication: Verifying the identity of diagnostic tools and users through secure authentication mechanisms.
- Integrity Checks: Ensuring that diagnostic data has not been tampered with during transmission.
3.3 What is the Role of Continuous Monitoring in Cybersecurity?
Continuous monitoring involves constantly tracking vehicle systems and networks for suspicious activity. This monitoring can help detect and respond to cyberattacks in real-time, minimizing potential damage.
3.4 How Does MERCEDES-DIAGNOSTIC-TOOL.EDU.VN Assist in Implementing These Practices?
MERCEDES-DIAGNOSTIC-TOOL.EDU.VN provides:
- Expert Guidance: Offering detailed information and best practices for implementing cybersecurity measures.
- Secure Diagnostic Tools: Providing access to diagnostic tools with built-in security features.
- Training Resources: Offering training programs to educate technicians on cybersecurity best practices.
- Support and Consultation: Providing ongoing support and consultation to help address specific cybersecurity challenges.
4. Technologies Used to Mitigate Vehicle Cybersecurity Vulnerabilities
Several technologies are available to mitigate vehicle cybersecurity vulnerabilities, including message encryption, intrusion detection systems, and secure over-the-air (OTA) updates.
4.1 What is Message Encryption and How Does It Work?
Message encryption involves encoding data transmitted within a vehicle’s network to prevent unauthorized access. Encryption algorithms scramble the data, making it unreadable to anyone without the decryption key.
4.2 How Do Intrusion Detection Systems Protect Vehicles?
Intrusion detection systems (IDS) monitor vehicle networks for suspicious activity, such as unauthorized access attempts or malicious code execution. When suspicious activity is detected, the IDS can alert the vehicle owner or security personnel, allowing them to take appropriate action.
4.3 Why Are Secure Over-the-Air (OTA) Updates Important?
Secure OTA updates allow automakers to remotely update vehicle software, including security patches, without requiring the vehicle to be physically connected to a diagnostic tool. This ensures that vehicles are always running the latest and most secure software versions.
4.4 How Does MERCEDES-DIAGNOSTIC-TOOL.EDU.VN Support the Use of These Technologies?
MERCEDES-DIAGNOSTIC-TOOL.EDU.VN supports these technologies by:
- Providing Compatible Tools: Offering diagnostic tools that support message encryption and secure communication protocols.
- Offering IDS Solutions: Providing access to intrusion detection systems designed for vehicles.
- Facilitating OTA Updates: Providing information and resources for performing secure OTA updates on Mercedes-Benz vehicles.
5. Addressing the Challenges of Vehicle Cybersecurity
Addressing vehicle cybersecurity involves overcoming several challenges, including the lack of transparency and collaboration within the automotive supply chain, the cost of implementing cybersecurity protections, and the need for continuous monitoring and updates.
5.1 What Are the Key Challenges in Vehicle Cybersecurity?
The key challenges include:
- Lack of Transparency: Limited communication and collaboration among automakers, suppliers, and security researchers.
- Cost of Implementation: The expense of incorporating cybersecurity protections into vehicle design and production.
- Complexity of Systems: The increasing complexity of vehicle systems makes it difficult to identify and mitigate all potential vulnerabilities.
- Evolving Threat Landscape: The constant emergence of new cyber threats requires continuous monitoring and adaptation.
5.2 How Can These Challenges Be Addressed?
These challenges can be addressed through:
- Enhanced Collaboration: Fostering greater transparency and collaboration among stakeholders in the automotive industry.
- Cost-Effective Solutions: Developing cost-effective cybersecurity solutions that can be easily integrated into vehicle design and production.
- Advanced Monitoring: Implementing advanced monitoring systems that can detect and respond to cyber threats in real-time.
- Regular Updates: Providing regular software updates to address newly discovered vulnerabilities.
5.3 What Industry-Led Efforts Are Underway to Improve Vehicle Cybersecurity?
Industry-led efforts include:
- Automotive Information Sharing and Analysis Center (ISAC): An organization that collects and analyzes threat intelligence and provides a forum for members to share vulnerability information.
- Cybersecurity Standards Development: Efforts to develop industry-wide cybersecurity standards and best practices.
- Collaboration with Security Researchers: Partnerships between automakers and security researchers to identify and address vulnerabilities.
5.4 How Does MERCEDES-DIAGNOSTIC-TOOL.EDU.VN Contribute to Overcoming These Challenges?
MERCEDES-DIAGNOSTIC-TOOL.EDU.VN contributes by:
- Providing Information and Resources: Offering detailed information on cybersecurity threats, best practices, and industry standards.
- Promoting Collaboration: Facilitating communication and collaboration among technicians, security researchers, and industry experts.
- Offering Secure Tools: Providing access to diagnostic tools with built-in security features and regular updates.
- Supporting Training and Education: Offering training programs to educate technicians on cybersecurity best practices.
6. The Role of Regulatory Bodies in Vehicle Cybersecurity
Regulatory bodies such as the National Highway Traffic Safety Administration (NHTSA) play a crucial role in vehicle cybersecurity by setting standards, providing guidance, and enforcing regulations to protect against cyber threats.
6.1 What Actions Has NHTSA Taken to Address Vehicle Cybersecurity?
NHTSA has taken several actions, including:
- Research and Development: Conducting research to identify and understand vehicle cybersecurity vulnerabilities.
- Guidance Development: Developing guidance to help the industry determine when cybersecurity vulnerabilities should be considered safety defects.
- Standards Examination: Examining the need for government standards or regulations regarding vehicle cybersecurity.
6.2 What Future Actions Are Planned by Regulatory Bodies?
Future actions may include:
- Implementing Cybersecurity Standards: Establishing mandatory cybersecurity standards for vehicle manufacturers.
- Enhancing Enforcement: Strengthening enforcement of cybersecurity regulations.
- Improving Collaboration: Fostering greater collaboration between government agencies, industry stakeholders, and security researchers.
6.3 How Does MERCEDES-DIAGNOSTIC-TOOL.EDU.VN Stay Informed About Regulatory Changes?
MERCEDES-DIAGNOSTIC-TOOL.EDU.VN stays informed through:
- Monitoring Regulatory Updates: Continuously tracking updates and announcements from regulatory bodies.
- Attending Industry Events: Participating in industry events and conferences to stay informed about the latest regulatory developments.
- Engaging with Regulatory Experts: Consulting with regulatory experts to understand and interpret regulatory changes.
7. Best Practices for Maintaining Vehicle Cybersecurity
Maintaining vehicle cybersecurity requires a proactive approach, including regular software updates, secure diagnostic practices, and awareness of potential threats.
7.1 Why Are Regular Software Updates Important?
Regular software updates are essential for addressing newly discovered vulnerabilities and ensuring that vehicles are protected against the latest cyber threats.
7.2 How Can Secure Diagnostic Practices Be Implemented?
Secure diagnostic practices include:
- Using Secure Tools: Employing diagnostic tools with built-in security features.
- Authenticating Users: Verifying the identity of users accessing diagnostic functions.
- Monitoring Access: Tracking and logging access to diagnostic systems.
- Securing Diagnostic Ports: Implementing security protocols for accessing the OBD port.
7.3 What Should Vehicle Owners Know About Cybersecurity?
Vehicle owners should:
- Keep Software Updated: Ensure that their vehicle’s software is always up-to-date.
- Be Aware of Phishing Scams: Be cautious of phishing scams that attempt to steal personal or vehicle data.
- Use Secure Networks: Avoid using unsecured Wi-Fi networks when connecting to vehicle systems.
- Report Suspicious Activity: Report any suspicious activity to the vehicle manufacturer or a qualified security professional.
7.4 How Does MERCEDES-DIAGNOSTIC-TOOL.EDU.VN Educate Vehicle Owners?
MERCEDES-DIAGNOSTIC-TOOL.EDU.VN educates vehicle owners by:
- Providing Informative Articles: Offering articles and guides on vehicle cybersecurity best practices.
- Offering Training Programs: Providing access to training programs that educate vehicle owners on cybersecurity threats and how to protect their vehicles.
- Offering Support and Consultation: Providing ongoing support and consultation to help vehicle owners address specific cybersecurity concerns.
8. The Future of Cybersecurity in Vehicle Diagnostics
The future of cybersecurity in vehicle diagnostics will likely involve increased automation, advanced threat detection, and greater collaboration among industry stakeholders.
8.1 What Trends Are Shaping the Future of Vehicle Cybersecurity?
Key trends include:
- Increased Automation: Automating cybersecurity tasks such as vulnerability scanning and threat detection.
- Artificial Intelligence (AI): Using AI to analyze vehicle data and identify potential cyber threats.
- Blockchain Technology: Employing blockchain to secure vehicle data and prevent tampering.
- Enhanced Collaboration: Fostering greater collaboration among automakers, suppliers, security researchers, and regulatory bodies.
8.2 How Will These Trends Impact Vehicle Diagnostics?
These trends will impact vehicle diagnostics by:
- Improving Security: Enhancing the security of diagnostic processes and preventing unauthorized access.
- Automating Threat Detection: Automating the detection of cyber threats during diagnostic sessions.
- Enhancing Data Integrity: Ensuring the integrity and confidentiality of diagnostic data.
- Facilitating Remote Diagnostics: Enabling secure remote diagnostics through advanced communication protocols.
8.3 How is MERCEDES-DIAGNOSTIC-TOOL.EDU.VN Preparing for the Future?
MERCEDES-DIAGNOSTIC-TOOL.EDU.VN is preparing by:
- Investing in Research and Development: Investing in research and development to stay ahead of emerging cybersecurity threats.
- Developing Advanced Tools: Developing advanced diagnostic tools with built-in security features and automation capabilities.
- Collaborating with Industry Experts: Collaborating with industry experts to develop innovative cybersecurity solutions.
- Offering Training and Education: Offering training programs to educate technicians on the latest cybersecurity trends and best practices.
9. Case Studies of Vehicle Cyberattacks
Examining case studies of vehicle cyberattacks provides valuable insights into the types of vulnerabilities that can be exploited and the potential consequences of a successful attack.
9.1 What Are Some Notable Examples of Vehicle Cyberattacks?
Notable examples include:
- The Jeep Cherokee Hack: Security researchers remotely hacked a Jeep Cherokee, demonstrating the ability to control the vehicle’s steering, brakes, and engine.
- The BMW ConnectedDrive Vulnerability: Researchers discovered a vulnerability in BMW’s ConnectedDrive system that allowed them to remotely unlock vehicle doors.
- The Tesla Hack: Security researchers demonstrated the ability to remotely control a Tesla vehicle’s features, including the lights, horn, and door locks.
9.2 What Lessons Can Be Learned from These Attacks?
Lessons learned include:
- Connectivity Increases Risk: Increased vehicle connectivity creates more opportunities for cyberattacks.
- Remote Access is Dangerous: Remote access vulnerabilities can allow attackers to control critical vehicle functions from anywhere in the world.
- Software Vulnerabilities are Common: Software vulnerabilities are a common entry point for cyberattacks.
- Proactive Security is Essential: Proactive security measures are essential for protecting against cyber threats.
9.3 How Can MERCEDES-DIAGNOSTIC-TOOL.EDU.VN Help Prevent Similar Attacks?
MERCEDES-DIAGNOSTIC-TOOL.EDU.VN can help prevent similar attacks by:
- Providing Secure Tools: Offering diagnostic tools with built-in security features.
- Offering Training and Education: Providing training programs to educate technicians on cybersecurity best practices.
- Offering Support and Consultation: Providing ongoing support and consultation to help address specific cybersecurity challenges.
- Promoting Awareness: Promoting awareness of cybersecurity threats and best practices among vehicle owners and technicians.
10. FAQs About Cybersecurity in Vehicle Diagnostics
Addressing frequently asked questions about cybersecurity in vehicle diagnostics can help clarify common misconceptions and provide valuable information to vehicle owners and technicians.
10.1 What is the Biggest Cybersecurity Threat to My Mercedes-Benz?
The biggest threat is unauthorized access to your vehicle’s systems through wireless connections or the OBD port, which could compromise safety-critical functions or steal personal data.
10.2 How Can I Tell if My Vehicle Has Been Hacked?
Signs include unusual vehicle behavior, such as erratic steering or braking, unauthorized access to vehicle data, and suspicious software updates.
10.3 What Should I Do if I Suspect My Vehicle Has Been Hacked?
Immediately disconnect your vehicle from all wireless networks, contact a qualified security professional, and report the incident to the vehicle manufacturer.
10.4 Are Older Vehicles Less Vulnerable to Cyberattacks?
While older vehicles have fewer connected features, they can still be vulnerable through the OBD port or aftermarket devices.
10.5 How Often Should I Update My Vehicle’s Software?
Update your vehicle’s software as soon as updates are available to ensure you have the latest security patches.
10.6 Can a Diagnostic Tool Introduce a Virus into My Vehicle?
Yes, if the diagnostic tool is not secure or has been compromised. Always use trusted and secure diagnostic tools.
10.7 What is the Role of the OBD Port in Vehicle Cybersecurity?
The OBD port provides direct access to vehicle systems, making it a potential entry point for cyberattacks if not properly secured.
10.8 How Does Encryption Protect My Vehicle’s Data?
Encryption scrambles data transmitted within the vehicle’s network, making it unreadable to unauthorized users.
10.9 What is Multi-Factor Authentication and Why is It Important?
Multi-factor authentication requires multiple verification methods to access vehicle systems, adding an extra layer of security against unauthorized access.
10.10 Where Can I Find More Information About Vehicle Cybersecurity?
You can find more information at MERCEDES-DIAGNOSTIC-TOOL.EDU.VN, which offers detailed guides, training programs, and expert support.
Understanding how cybersecurity impacts your vehicle’s diagnostics is crucial in today’s interconnected world. Stay informed, implement best practices, and utilize secure diagnostic tools to protect your Mercedes-Benz.
Ready to enhance your Mercedes-Benz cybersecurity? Contact us at MERCEDES-DIAGNOSTIC-TOOL.EDU.VN for expert consultation on diagnostic tools, hidden feature unlocking, and maintenance guidance.
Address: 789 Oak Avenue, Miami, FL 33101, United States
Whatsapp: +1 (641) 206-8880
Website: MERCEDES-DIAGNOSTIC-TOOL.EDU.VN